Scope of Service
The scope of the Web Application Assessment service includes web sites specified by the customer. Ingram Micro performs the Web Application Assessment in two formats:
-
External Web Application Assessment: Performed remotely against customer’s web site(s) that are publicly accessible.
-
Internal Web Application Assessment: Performed from within the premises of the target organization. This type of scanning is usually performed against web sites and application accessible to organization employees, contractors, and guests from within organization’s network such as internal portal.
Process of Assessment
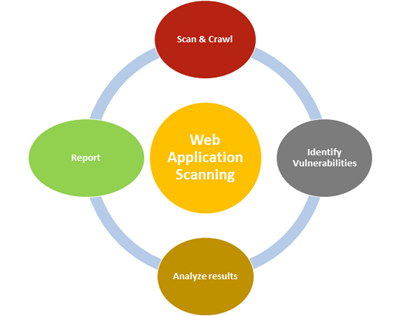
Web Application Assessment is usually performed according to the following steps as follow:
-
Scan and crawl: gather information about the running web application including network ports, web server version, installed modules, version numbers, and crawl through all folders and files that may exist on the web site.
-
Identify Vulnerabilities: building on information gathered in the previous phase, we will assess the existence of web vulnerabilities or security misconfiguration by sending specially crafted requests to the web application in an attempt to identify vulnerabilities and security weaknesses.
-
Result Analysis: Review of the application responses to web requests made in the previous phase, and manually verify the identified web vulnerabilities and eliminate false positives.
-
Report: report identified web vulnerabilities including impact rating and recommended action to mitigation them.
Ingram Micro will use a combination of automated and manual methods for identifying web related vulnerabilities and eliminating false positives. The following diagram summarize the phases of Web Application Assessment service:
Deliverables
Upon completion of the Web Application Assessment, a detailed report is sent to the client including the following:
-
Executive Summary: Summary of the purpose of this assessment, as well as brief explanation of the threats that the organization is exposed to from a business perspective.
-
Findings: A detailed, technical explanation of the findings of the assessment along with steps and proofs of the findings.
Conclusion & Recommendations: This section provides final recommendations and summary of the issues found during the security assessment.
Service Delivery Time
The Web Application Assessment service on about 5 Web Applications can be completed in three business days.
Book Assessment Services from Ingram Micro