Scope of Service
The Policy Compliance Audit service is applicable to external and internal device in the organization.
Process of Compliance Audit
Policy Compliance Audit will be performed using industry standard tools (e.g. Qualys) and will consist of the following steps:
Step 1: Scope Validation:
Customer will provide a list of all Internet-facing and internal IP addresses and/or IP address ranges to be included in service scope. Ingram Micro team will validate the scope of the target list and conducts network probing to determine which hosts and services are active. Ingram Micro team will perform following activities:
-
Ping sweeps, port scans, and route tracing.
-
Foot printing of networks and systems.
-
Searches for internet domain name registration.
-
Searches for internet registry numbers.
-
Domain name service (DNS) lookups.
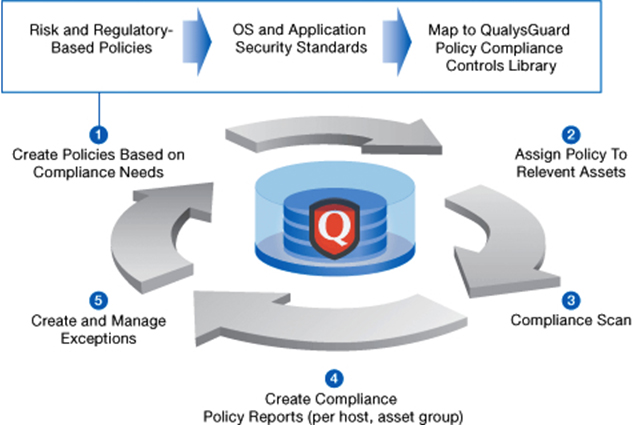
Step 2: Performing Compliance Audit
Ingram Micro team will create a compliance policy based on the organization’s compliance needs, and assign relevant assets to that policy. For example, following few policies are added to test Policy compliance of CIS Standard:
-
CIS Benchmark for Oracle Database 11g R2 Microsoft Windows V2.0.0
-
CIS Benchmark for Oracle Database 11g R2 Linux V2.0.0
-
CIS – Cisco IOS 15, V4.0.0
-
CIS Benchmark for CentOS Linux 6, v1.0.0
-
CIS Benchmark for Oracle Database server11-11g R2, V1.0.0
-
CIS Benchmark for Oracle Solaris 10, V5.1.0
-
CIS Benchmark for Red Hat Enterprise Linux 6, v1.#.0
-
CIS Benchmark for SuSE Enterprise Linux Server 10.x v2.0
-
CIS Benchmark for SuSE Enterprise Linux Server 11.x V1.1.0
Policy compliance Audit will be performed based on the created Policy, the customer requirements, and policy standards and can be scheduled on a regular basis.
Step 3: Gap Analysis
In this step, Ingram Micro team will learn about the environment and determine vulnerabilities that are present. Some vulnerabilities will be apparent by just using the information learned from the first two steps. However, many vulnerabilities can only be investigated with probe-and-response testing. In this type of test, Ingram Micro team will send data to a service or application and look for a certain response that indicates the presence of a vulnerability.
Step 4: Reporting
After analysis of vulnerabilities, Ingram Micro team will provide a detailed report of security issues discovered in the network which may lead to non-compliance of any policy. Recommendations are also provided to comply with the policies.
Deliverables
Upon completion of the Policy Compliance Audit, a detailed report is sent to the client which includes the following results:
Policy Summary: It provides a one-page summary of your compliance status for a specific policy
Authentication Report: The Authentication Report indicates whether authentication was successful for scanned hosts. If authentication to a host is successful, then the host can be evaluated for compliance.
Compliance Score Card Report: Gives report on multiple policies in a single report and compliance score across selected policies for specific environments
Control Pass/Fail Report: Gives the report on status of the control whether pass or fail.
Recommendations Report: Detailed report on recommendations will be provided to fix the non-compliance.
Service Delivery Time
The Policy Compliance Service for 10 IT Assets can be completed in 2 business days.
Book Assessment Services from Ingram Micro