Scope of Service
Depending on the service level purchased by the SP and/or end-client, Ingram Micro SOC will perform the below services as part of its engagement.
Security Monitoring, Incident Management & Events of Interest
-
Perform 24x7 logs & audit trails monitoring for security events to detect the known, as well as unknown attacks
-
Raise alerts for any suspicious events that may lead to security breach in customer environment
-
Perform 24x7 performance and service availability monitoring, so that desired state and integrity of devices and services levels can be maintained
-
Monitor alerts and events reported by devices under scope, troubleshoot, recommend remedial action, and provide rapid response to incidents
-
Monitor and detect events of interest that are anomaly based, and are unusual & suspicious in nature.
-
Initiate prompt corrective measures to stop or prevent attacks
-
Prepare and publish daily, weekly, and/or monthly customs reports to summarize list of incidents, security advisories, change management, and other security recommendations
-
Provide operations trend analysis and correlation reports of operations data, for previous months vs. current month
Log Analysis and Management
A log, in a computing context, is the automatically produced and time-stamped documentation of events relevant to a particular system. Virtually all software applications and systems produce log files. Log management is the collective processes and policies used to administer and facilitate the generation, transmission, analysis, storage, archiving and ultimate disposal of the large volumes of log data created within an information system. Systems in scope include:
-
Intrusion detection and/or prevention system
-
Antivirus software
-
Firewalls, routers, and other network devices
-
VPN, secure gateways, and file transfer servers
-
Application servers, web servers, database servers
-
Operating systems, virtual machines, and physical workstations serving as user end-points
Security Device Management
Security device management service addresses security monitoring and management of security devices and systems. Devices include firewalls, IDS/ IPS, WAF, SIEM, anti-virus & malware, and VPN.
Ingram Micro collaborates with SP and/or end-client service delivery and SOC teams to establish a backup and restore management process, including schedule requirements for configuration backup and ad-hoc backups (as required), based on change management or troubleshooting needs. Activities performed include:
-
Validate signatures and review configurations
-
Do device upgrades and patch management
-
Perform incident tracking and correlation
-
Provide regular updates on attack signatures
-
Provide on-demand device reports for devices, security, and compliance
-
Do analysis and correlation, as well as alert escalation and prioritization
-
Detect unauthorized access to network resources
-
Evaluate SANS 20 critical security controls on the devices-in scope
-
Evaluate applications against OWASP top 10
Vulnerability Assessment
The objective of a vulnerability assessment is to validate host configurations and produce a list of known vulnerabilities existing on systems that are in scope. The testing is limited to relatively safe checks designed to limit any negative impact to environments.
Execution:
A technical network security assessment is performed to identify critical flaws in customer network that an attacker could exploit. Testing may be conducted on any networked device, firewalls, routers or other network infrastructure devices, intrusion detection & prevention systems, web servers, email systems, virtual private networking (VPN) systems, etc., Ingram Micro SOC will use a combination of automated and manual scanning methods with commercial and publicly available tools, as well as custom scripts and applications that were developed by Ingram Micro.
Vulnerability Assessment: Step 1 - Scope Validation
Ingram Micro SOC team will validate the scope of the target list that was provided. This is a safety measure and will ensure the accuracy of subsequent findings. Ingram Micro will perform following activities:
-
Ping sweeps, port scans, and route tracing
-
Foot printing of networks and systems
-
Searches for internet domain name registration
-
Searches for internet registry numbers
-
Domain name service (DNS) lookups
Vulnerability Assessment: Step 2 - Network Discovery
Ingram Micro SOC will validate targets within the IP address range listed in scope. Ingram Micro performs this step to attempt to identify live hosts for future testing efforts. Activities performed by Ingram Micro include:
-
Scan a range of IP addresses to identify top TCP ports in use
-
Identify applications and potential version information through banner grabbing
-
Assemble a list of potential targets for further testing
After the scan, Ingram Micro SOC will deliver the list of live hosts with the top ports in use, suitable for inclusion into the final report.
Vulnerability Assessment: Step 3 - Enumeration & Vulnerability Mapping
Enumeration involves actively trying to identify services that are running, applications used, version numbers, service banners, etc., Testing in this phase is to look for more noticeable reconnaissance activities that typically precede an attack.
In vulnerability mapping, Ingram Micro learns about the environment and determines vulnerabilities that are present. Some vulnerabilities will be apparent by just using the information learned from the first two steps. However, many vulnerabilities can only be investigated with probe-and-response testing. In this type of test, Ingram Micro will send data to a service or application and looks for a certain response that indicates a vulnerability may be present.
Vulnerability Assessment: Step 4 - Manual Verification
Automated scanning tools often report false positives – i.e. reported vulnerabilities that are not actually present. For vulnerabilities discovered through automated scanning, Ingram Micro takes steps to ensure reported vulnerability findings are an accurate representation of customer’s environment. Without this often overlooked step, significant time may be wasted attempting to remediate vulnerabilities that don’t exist.
Web Application Scanning
Ingram Micro's web application scanning service leverages industry-leading application scanning tools and technology (e.g. Qualys) to assess the network security of customer’s web applications and identify flaws that could threaten their online presence and/or the confidentiality of information. These services help identify vulnerabilities with web applications and thus enable the customers to secure their web applications while maintaining compliance. Services and capabilities include:
-
Provide 24x7 support to address new and existing threats and vulnerabilities
-
Provide expertise on vulnerability management from scan to remediation of vulnerabilities
-
Track vulnerabilities to resolution with remediation tracking
-
Provide internal and external scanning to get a 360-degree view of network vulnerabilities
-
Provide configurable scans for customized audits
-
Leverage out-of-the-box integration with existing and legacy security management consoles
-
Provide access via a web browser anytime, anywhere
Penetration Scanning
Penetration testing is performed to determine the resilience of the network perimeter against threats from remote attackers over the internet. It first models and tests potential technical attack vectors that typically have a goal to breach the perimeter security and gain unauthorized access to systems and sensitive data. In addition to traditional direct attacks at the network, operating system, and applications, certain client side tests will also be conducted to test the effectiveness of virus and malware screening systems and e-mail proxies.
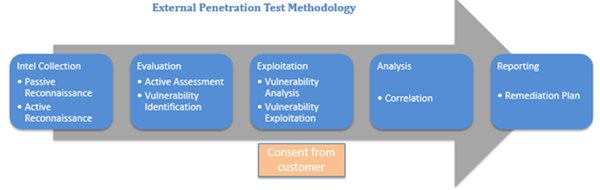
External penetration testing techniques include, but are not limited to:
-
Perform information gathering on networks associated with the customer organization using sources such as DNS, WHOIS, Usenet news, and public websites
-
Iteratively identify and analyze accessible systems on identified networks
-
Analyze hosts for operating system, configuration and daemon vulnerabilities
-
Exploit, where appropriate, any security vulnerabilities which provide escalated privileges or network visibility, such as access to the DMZ or internal network
-
Conduct a series of scenario analysis based on the information retrieved, such as attempting access to internal servers, customer records, or performing web site defacement
Internal penetration testing techniques include, but are not limited to:
-
Perform information gathering on internal networks to discover live systems covering wired and wireless environment
-
Iteratively identify and analyze accessible systems on identified networks
-
Analyze hosts for operating system, configuration and running services
-
Enumerate services and platforms
-
Identify known vulnerabilities on running systems
- Exploit, where appropriate, any security vulnerabilities which provide escalated privileges
Hardening and Standardizations
This service provides well-defined, un-biased and consensus-based industry best practices to help organizations assess and improve their security. Resources include secure configuration benchmarks, automated configuration assessment tools and content and security metrics.
While many laws and standards require organizations to ensure that their servers, workstations and network infrastructure devices are configured in a secure manner, however, they don't provide prescriptive guidance on exactly how to achieve that level of security. Organizations instead rely on prescriptive security standards – such as CIS benchmarks, DISA STIGs, and internal minimum security requirements – to ensure that appropriate controls are applied.
After suggested hardening steps are implementing as per the above hardening standards, Ingram Micro also performs a penetration test to identify any further gaps and arrive at “cyber-attack readiness”.
Compliance Reporting
Ingram Micro compliance reporting services are built on pre-defined and canned compliance report templates such as PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001 etc. It is done by collecting, analyzing and archiving Windows event logs and syslogs received from customer’s network infrastructure.
The solution helps organizations to retain and/or archive log data for a custom time period. Archiving log data for flexible time period helps administrators to perform forensic analysis on the archived logs to meet compliance audit requirements, investigate data thefts, and to track network intruders.
Book Assessment Services from Ingram Micro