Scope of Service
The scope of the Vulnerability Assessment service includes all IT assets that are connected to the organization’s network. Vulnerability Assessment provides an insight into an organization’s current state of security, and the effectiveness of its countermeasures. Vulnerability Assessments is performed in two formats:
-
External Vulnerability Assessment: Performed remotely with no internal access provided to our SOC team. The goal of this test is to identify and classify the weaknesses of the internet-facing IT assets of an organization such as Web applications, web servers, network endpoints, VPN, and e-mail servers. This test helps an organisation to learn what external IT assets need security controls, patches, and general hardening.
-
Internal Vulnerability Assessment: Performed from within the premises of the target organization, usually to identify and classify threats and weaknesses in the internal network. It helps an organisation determine its compliance to global or local policies, standards and procedures in terms of information security, data protection and segmentation of networks.
Process of Assessment
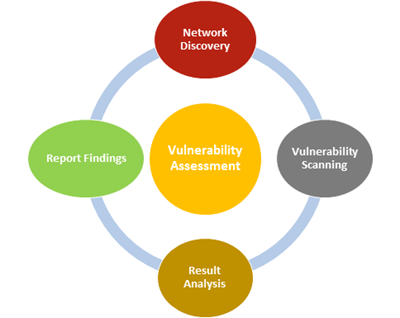
Vulnerability Assessment is usually performed according to the following steps:
-
Network Discovery: discover IT assets connected to the network and confirm those assets with organization to ensure validity.
-
Vulnerability Scanning: scan the identified IT assets against known security vulnerabilities.
-
Result Analysis: Review of identified vulnerabilities and eliminate false positives.
-
Report Finding: report identified vulnerabilities including impact rating and recommended action to mitigation them.
Deliverables
Upon completion of the Vulnerability Assessment, a detailed report is sent to the client including the following:
Executive Summary: Summary of the purpose of this assessment, as well as brief explanation of the threats that the organization is exposed to from a business perspective.
Findings: A detailed, technical explanation of the findings of the assessment along with steps and proofs of the findings.
Conclusion & Recommendations: This section provides final recommendations and summary of the issues found during the security assessment.
Service Delivery Time
The Vulnerability Assessment service on about 100 IT Assets can be completed in two business days.
Book Assessment Services from Ingram Micro